The Collapse of Silicon Valley Bank
The Pragmatic Engineer
MARCH 13, 2023
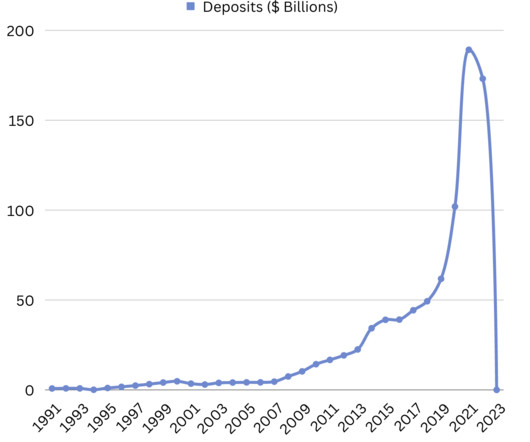
The FDIC stated “all insured depositors will have full access to their insured deposits no later than Monday morning, March 13, 2023.” ” This meant companies had guaranteed access to $250K on their account, but everything else was uncertain. This was bad news and the implications were just starting to become clear.












































Let's personalize your content