The Collapse of Silicon Valley Bank
The Pragmatic Engineer
MARCH 13, 2023
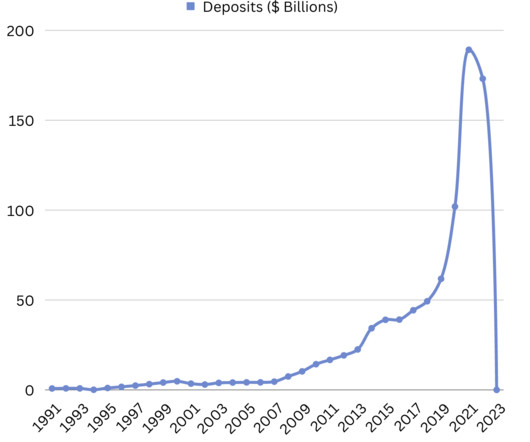
The bank’s systems start to be overloaded to the point of customers not being able to log on and transfer. The FDIC is a government agency whose goal is to maintain stability and public confidence in the US financial system. For some startups, losing access to their bank account prompted drastic action.













































Let's personalize your content