Demystifying Azure Storage Account network access
Towards Data Science
OCTOBER 30, 2024
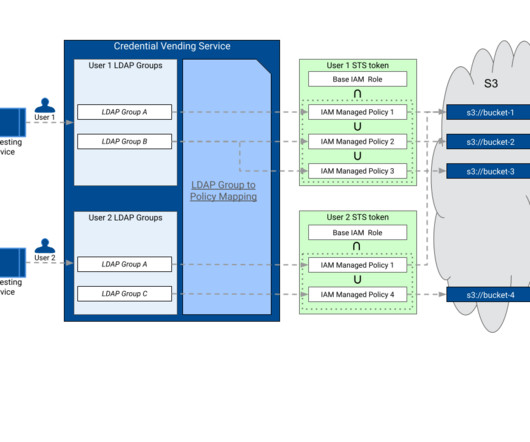
Demystifying Azure Storage Account Network Access Service endpoints and private endpoints hands-on: including Azure Backbone, storage account firewall, DNS, VNET and NSGs Connected Network — image by Nastya Dulhiier on Unsplash 1. Defense in depth measures must be in place before data scientists and ML pipelines can access the data.












































Let's personalize your content