What are Data Access Object and Data Transfer Object in Python?
Analytics Vidhya
FEBRUARY 6, 2023
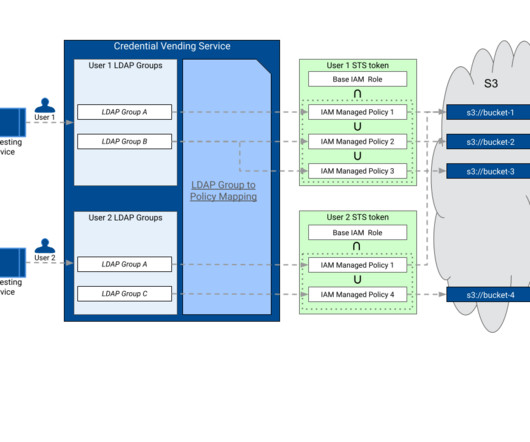
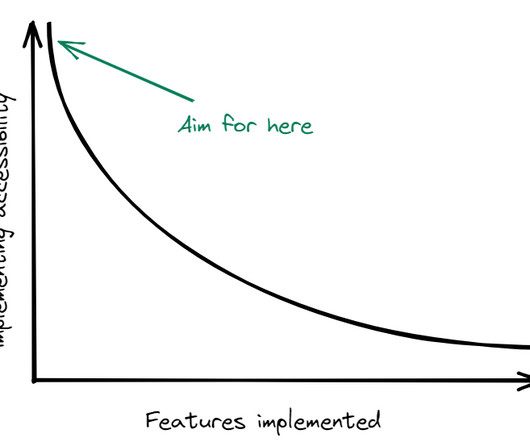
This ensures easy […] The post What are Data Access Object and Data Transfer Object in Python? The pattern is not an actual code but a template that can be used to solve problems in different situations. Especially while working with databases, it is often considered a good practice to follow a design pattern.













































Let's personalize your content