Convert Bytes to String in Python: A Tutorial for Beginners
KDnuggets
JULY 15, 2024
But sometimes, you may need to work with bytes instead. Let’s learn how to convert bytes to string in Python. Strings are common built-in data types in Python.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
 Bytes Related Topics
Bytes Related Topics 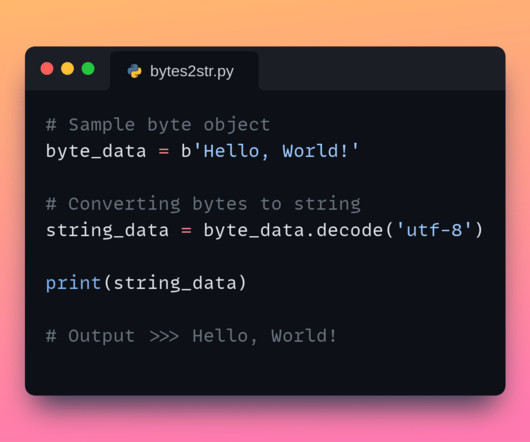
KDnuggets
JULY 15, 2024
But sometimes, you may need to work with bytes instead. Let’s learn how to convert bytes to string in Python. Strings are common built-in data types in Python.
The Pragmatic Engineer
NOVEMBER 21, 2023
Rather than failing with an error, this encountered an existing bug in the DEC Unix “copy” (cp) command, where cp simply overwrote the source file with a zero-byte file. After this zero-byte file was deployed to prod, the Apache web server processes slowly picked up the empty configuration file.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Agent Tooling: Connecting AI to Your Tools, Systems & Data
How to Modernize Manufacturing Without Losing Control
Mastering Apache Airflow® 3.0: What’s New (and What’s Next) for Data Orchestration

Confluent
APRIL 11, 2023
If you've used Kafka Streams, Kafka clients, or Schema Registry, you’ve probably felt the frustration of unknown magic bytes. Here are a few ways to fix the issue.
Netflix Tech
JULY 8, 2020
By Torio Risianto, Bhargavi Reddy, Tanvi Sahni, Andrew Park Continue reading on Netflix TechBlog ».

Confluent
SEPTEMBER 24, 2021
This release includes a major upgrade to ksqlDB’s foreign-key joins, the new data type BYTES, and a new ARRAY_CONCAT function. We’re pleased to announce ksqlDB 0.21.0! All of these features […].

Emeritus
DECEMBER 20, 2021
Kira Radinsky of Diagnostic Robotics Chairwoman & CTO, shared, “My true passion is arming humanity with scientific capabilities to automatically anticipate,… The post Exploring Careers in Data Science One Byte at a Time appeared first on Emeritus Online Courses.

Scott Logic
NOVEMBER 23, 2023
Cost increases when gradient accumulation is enabled, or becomes ~free if used in concert with DDP DDP usually costs ~4 bytes/param, but becomes cheaper if used in concert with AMP DDP can be made 2.5 Transformer Math does not mention a "4 bytes/param master gradients" cost.
Netflix Tech
DECEMBER 14, 2020
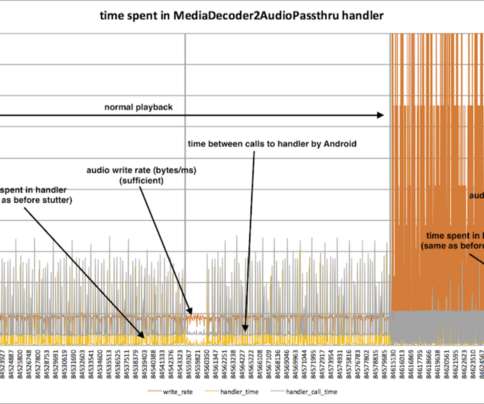
Figure 2: Visualizing Audio Throughput and Thread Handler Timing The orange line is the rate that data moved from the streaming buffer into the Android audio system, in bytes/millisecond. You can see three distinct behaviors in this chart: The two, tall spiky parts where the data rate reaches 500 bytes/ms.

Engineering at Meta
MAY 22, 2024
Challenges Large packet size One of the main challenges is the size of the Kyber768 public key share, which is 1184 bytes. This is close to the typical TCP/IPv6 maximum segment size (MSS) of 1440 bytes, but is still fine for a full TLS handshake. However, the key size becomes an issue during TLS resumption.
Towards Data Science
MARCH 5, 2024
Like a dragon guarding its treasure, each byte stored and each query executed demands its share of gold coins. Join as we journey through the depths of cost optimization, where every byte is a precious coin. It is also possible to set a maximum for the bytes billed for your query. Photo by Konstantin Evdokimov on Unsplash ?

WeCloudData
FEBRUARY 13, 2025
quintillion bytes of data are generated every day and thats a great sign for anyone interested in a data-driven career. The world is becoming increasingly reliant on data, about 2.5 There are many career paths related to data including data scientist, data analyst, ML engineer, AI engineer, BI engineer, and many more.
WeCloudData
MARCH 1, 2025
quintillion bytes of data are generated every day. The world is becoming increasingly dependent on data, about 2.5 Data is shaping our decisions, from personalized shopping experiences to checking weather forecasts before leaving home. All of these data science applications have a life cycle to follow.
LinkedIn Engineering
JUNE 15, 2023
An Avro file is formatted with the following bytes: Figure 1: Avro file and data block byte layout The Avro file consists of four “magic” bytes, file metadata (including a schema, which all objects in this file must conform to), a 16-byte file-specific sync marker, and a sequence of data blocks separated by the file’s sync marker.

Confluent
JULY 24, 2019
The only difference between the KafkaSender and any other Jaeger provided ThriftSender is that rather than sending messages to Jaeger directly, the KafkaSender takes the span batch bytes and produces a message to the Kafka topic: tracing-topic. Then, it passes the message value byte array to the JaegerHttpSender.
Netflix Tech
SEPTEMBER 18, 2024
The first level is a hashed string ID (the primary key), and the second level is a sorted map of a key-value pair of bytes. Smarter Pagination We chose payload size in bytes as the limit per response page rather than the number of items because it allows us to provide predictable operation SLOs.

Cloudera
MARCH 2, 2022
For instance, in both the struct s above the largest member is a pointer of size 8 bytes. Total size of the Bucket is 16 bytes. Similarly, the total size of DuplicateNode is 24 bytes. However 12 bytes is not a valid size of Bucket , as it needs to be a multiple of 8 bytes (the size of the largest member of the struct ).

Tweag
NOVEMBER 22, 2023
rwxr-xr-x 1 jherland users 31560 Jan 1 00:00 hello.with-g We can see that the debug symbols add an extra (31560 - 8280 =) 23280 bytes (or almost 300%) to the final executable. gnu_debuglink ) has been added, and comparing the file sizes we see that this costs a modest 96 bytes. compared to hello.default ). What is removed?

U-Next
MARCH 16, 2023
Input and Output Streams: An input stream of bytes is represented by the abstract superclass InputStream of the java.io package’s OutputStream class is the abstract superclass that describes an output bytes stream. The next byte accessible as stream int is returned by this procedure.

Netflix Tech
FEBRUARY 13, 2020
The goal is to have the compressed image look as close to the original as possible while reducing the number of bytes required. Shown below is one original source image from the Kodak dataset and the corresponding result with JPEG 444 @ 20,429 bytes and with AVIF 444 @ 19,788 bytes.

Engineering at Meta
FEBRUARY 20, 2024
In the new representation , the first four bytes of the view object always contain the string size. Otherwise, a prefix of the string is stored in the next four bytes, followed by the buffer ID (StringViews can contain multiple data buffers) and the offset in that data buffer. first writing StringView at position 2, then 0 and 1).

Engineering at Meta
APRIL 17, 2023
It computes ingress and egress total bytes and ingress ECN-marked bytes from the lengths and CE bits of the packets. Millisampler collects a variety of metrics. Millisampler also sounds TTLd marked retransmits. Millisampler uses a 128-bit sketch to estimate the number of active (incoming and outgoing) connections.
Pinterest Engineering
NOVEMBER 22, 2023
See the graph below, which shows the compaction read and write bytes on a cluster when it is bootstrapping for the first time. Figure 10: compaction read and write bytes showing non zero values as soon as host starts up. However, we observed compaction starting as soon as SSTs were getting ingested.

Pinterest Engineering
APRIL 7, 2025
At Pinterest, we have an in-house rate limiter implementation: it maintains a budget (number of credits) based on the configured rate (bytes per second) and the time elapsed in between requests. It exposes an interface for conducting rate limiting when interacting with S3.

Netflix Tech
MARCH 6, 2019
That is, all mounted files that were opened and every single byte range read that MezzFS received. Finally, MezzFS will record various statistics about the mount, including: total bytes downloaded, total bytes read, total time spent reading, etc. Actions ?—?MezzFS The different colors mean different things?—?green

Rock the JVM
DECEMBER 17, 2023
The UDP header is fixed at 8 bytes and contains a source port, destination port, the checksum used to verify packet integrity by the receiving device, and the length of the packet which equates to the sum of the payload and header. flip () println ( s "[server] I've received ${content.limit()} bytes " + s "from ${clientAddress.toString()}!

Tweag
JANUARY 18, 2023
reading and writing to a byte stream). Say we have some arbitrary Python class, a first approximation may be to define encode and decode methods: from typing import Self class MyClass : def encode ( self ) - > bytes : # Implementation goes here. classmethod def decode ( cls , data : bytes ) - > Self : # Implementation goes here.

Engineering at Meta
JANUARY 26, 2023
Chart 2: Bytes logged per second via Legacy versus Tulip. We can see that while the number of logging schemas remained roughly the same (or saw some organic growth), the bytes logged saw a significant decrease due to the change in serialization format. Chart 1: Logging schemas using Legacy versus Tulip.
Netflix Tech
MARCH 28, 2025
Drawing an analogy to Byte Pair Encoding (BPE) in NLP, we can think of tokenization as merging adjacent actions to form new, higher-level tokens. Tokenizing User Interactions : Not all raw user actions contribute equally to understanding preferences. Tokenization helps define what constitutes a meaningful token in a sequence.

Engineering at Meta
SEPTEMBER 12, 2023
We needed to turn this 8-byte write vulnerability into something useful for an attacker. This is important because it means we can use the 8-byte write primitive to corrupt and control its value. Any VR application can trigger this vulnerability by sending a specially crafted SetPerformanceIdealFeatureState Runtime IPC message.
Netflix Tech
SEPTEMBER 24, 2021
The index file keeps track of the physical location (URL) of each chunk and also keeps track of the physical location (URL + byte offset + size) of each video frame to facilitate downstream processing. What happens when the packager references bytes that have already been uploaded (e.g. when it updates the ‘mdat’ size)?
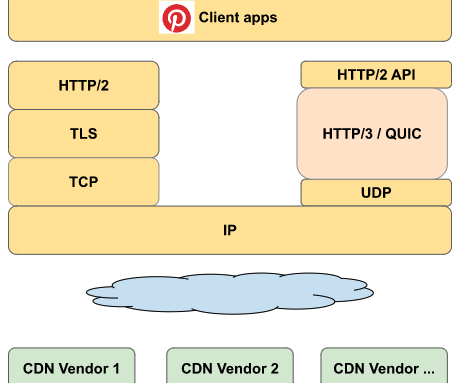
Pinterest Engineering
FEBRUARY 23, 2023
How Does HTTP/3 Help HTTP/3 is a modern HTTP protocol that has many advantages compared to HTTP/2, including but not limited to: No TCP head of line blocking problem in comparison to HTTP/2 Connection migration across IP addresses, which is good for mobile use cases Able to change/tune Lost detection and Congestion control Reduced connection time (0-RTT, (..)

Lyft Engineering
MARCH 11, 2024
The diff_bytes is 0 now! We now need to reset sequences in, which we accomplished with the following script: [link] This ensures that the sequence starts from the last entry of the individual tables.

Confluent
FEBRUARY 12, 2019
Bytes, Decimals, Numerics and oh my. Bytes, Decimals, Numerics and oh my. So our DECIMAL becomes a seemingly gibberish bytes value. By default, Connect will use its own DECIMAL logical type, which is serialised to bytes in Avro. Resetting the point from which JDBC source connector reads data. Changing the topic name.

Cloudera
JANUARY 17, 2024
By using component_name and “Hello World Prometheus,” we’re monitoring the bytes received aggregated by the entire process group and therefore the flow. Select the nifi_amount_bytes_received metric. Use the label filters to narrow down the component in the flow.

DoorDash Engineering
JANUARY 16, 2024
This led us to use a number of observability tools, including VPC flow logs , ebpf agent metrics , and Envoy networking bytes metrics to rectify the situation. Nonetheless, combining network bytes metrics from different sources can be enough to identify hotspots that, when addressed, can make a material dent in usage and cost.

Snowflake
FEBRUARY 27, 2024
For example, you can specify billing events in your app code and charge consumers based entirely on their usage of your application. This is a flexible, usage-based pricing model to allow providers to price-to-value their applications.

Confluent
MAY 29, 2019
zip Zip file size: 3593 bytes, number of entries: 9 drwxr-xr-x 2.0 unx 2312 b- defN 19-Feb-13 13:05 ksql-script.sql 9 files, 5502 bytes uncompressed, 2397 bytes compressed: 56.4%. . ==> zipinfo ksql/build/distributions/ksql-pipeline-1.0.0.zip zip Zip file size: 3593 bytes, number of entries: 9 drwxr-xr-x 2.0

DoorDash Engineering
AUGUST 15, 2023
We also have an unmarshalling function to convert the raw bytes from the kernel into our structure. sk) { return 0; } u64 key = (u64)sk; struct source *src; src = bpf_map_lookup_elem(&socks, &key); When capturing the connection close event, we include how many bytes were sent and received over the connection.

Workfall
SEPTEMBER 26, 2023
We’re taking in 16 bytes of data at a time from the stream. This function will provide basic units of data in the form of raw bytes. These bytes can then be converted into a readable JSON format. This will transfer information in one go over an HTTP connection from the server to the client.
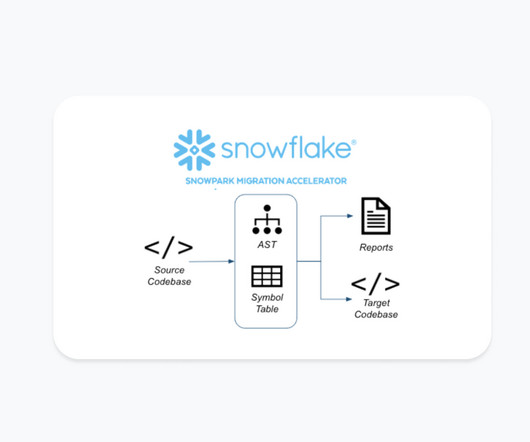
Snowflake
JUNE 20, 2024
If there is a substantial amount of extra code files or the total size (in byte) of the files being scanned is extremely large, the Snowpark Migration Accelerator could run out of internal resources on the machine processing the code. For conversion, if you’re just getting started, start small.
Towards Data Science
APRIL 11, 2023
Job information after creating a clustered table(Image by author) Execution details after creating a clustered table(Image by author) From the job info and execution details, you can see the number of bytes processed and records scanned reduced significantly(from 1.5 GB to 55 MB and 7M to 260k).

Knowledge Hut
MARCH 7, 2024
quintillion bytes (or 2.5 With the rise in opportunities related to Big Data, challenges are also bound to increase. Below are the 5 major Big Data challenges that enterprises face in 2024: 1. The Need for More Trained Professionals Research shows that since 2018, 2.5 exabytes) of information is being generated every day.

Confluent
APRIL 3, 2019
KsqlTopic.source.deserializer","time":1552564841423,"message":{"type":0,"deserializationError":{"errorMessage":"Converting byte[] to Kafka Connect data failed due to serialization error: ","recordB64":null},"recordProcessingError":null,"productionError":null}}. 5476133448908187392.KsqlTopic.source.deserializer","time":1552564841423,"message":{"type":0,"deserializationError":{"errorMessage":"Converting
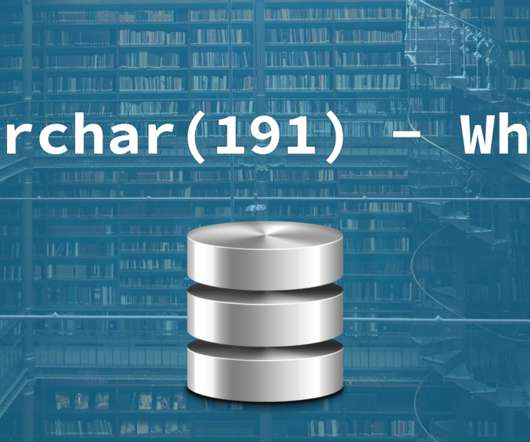
Grouparoo
MAY 13, 2021
However, the the most popular text encoding ( Latin1 or utf8 ) on the most popular MySQL database engine ( innodb ) assumed that 3 bytes was enough to store every character 2 , and once utf8mb4 came along with characters like ? 4 bytes were needed to store each character. Specifically, 767/4 = 191 characters!
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?

Let's personalize your content