Netflix Cloud Packaging in the Terabyte Era
Netflix Tech
SEPTEMBER 24, 2021
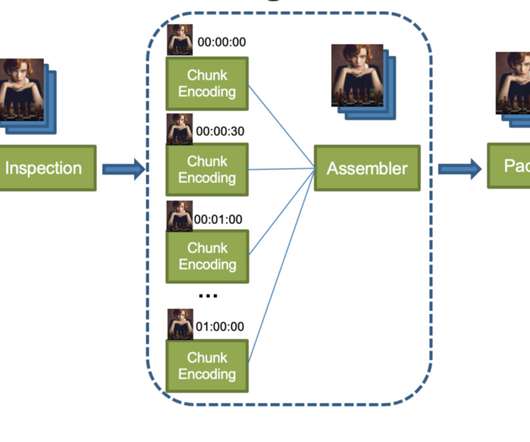
Lastly, the packager kicks in, adding a system layer to the asset, making it ready to be consumed by the clients. From chunk encoding to assembly and packaging, the result of each previous processing step must be uploaded to cloud storage and then downloaded by the next processing step.





























Let's personalize your content