Top 10 Examples of Cloud Computing
Knowledge Hut
APRIL 23, 2024
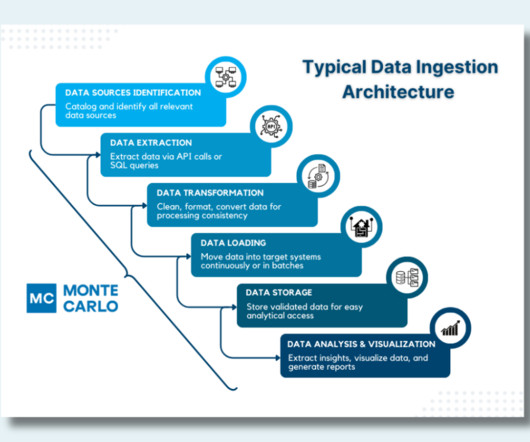
Cloud Computing Examples Cloud computing consists of several examples that help in data storage over the internet seamlessly. File Sharing + Data Storage: Dropbox File sharing is another fine example of cloud computing platform. It aims to make business procedures secure and reliable and maintains data security.





















Let's personalize your content