10 Python Libraries Every Data Scientist Should Know
KDnuggets
AUGUST 12, 2024
Want to take the next step in your journey to becoming a data scientist? Check out these Python libraries for data science that you can't do without.

KDnuggets
AUGUST 12, 2024
Want to take the next step in your journey to becoming a data scientist? Check out these Python libraries for data science that you can't do without.
databricks
AUGUST 12, 2024
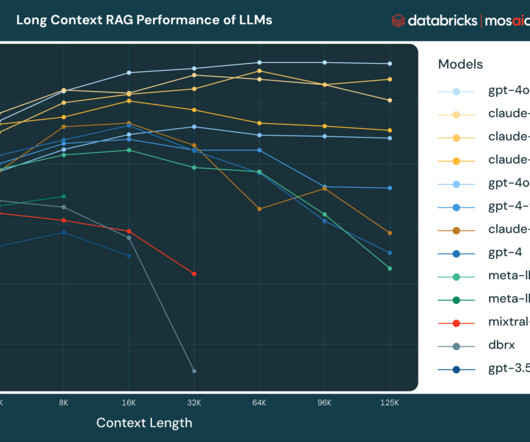
Retrieval Augmented Generation (RAG) is the most widely adopted generative AI use case among our customers. RAG enhances the accuracy of LLMs by.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

KDnuggets
AUGUST 12, 2024
Today, we’re looking for five quality resources that will teach you advanced SQL and do it for free.

databricks
AUGUST 12, 2024
The blog explores data streams from NASA satellites using Apache Kafka and Databricks. It demonstrates ingestion and transformation with Delta Live Tables in SQL and AI/BI-powered analysis of supernova events.

Speaker: Tamara Fingerlin, Developer Advocate
Apache Airflow® 3.0, the most anticipated Airflow release yet, officially launched this April. As the de facto standard for data orchestration, Airflow is trusted by over 77,000 organizations to power everything from advanced analytics to production AI and MLOps. With the 3.0 release, the top-requested features from the community were delivered, including a revamped UI for easier navigation, stronger security, and greater flexibility to run tasks anywhere at any time.

KDnuggets
AUGUST 12, 2024
Why NumPy is significantly faster than standard Python code execution.

ArcGIS
AUGUST 12, 2024
Use the ArcGIS Network Analyst route solver and out-of-the-box tools to calculate travel time and distance between origin-destination pairs.
Data Engineering Digest brings together the best content for data engineering professionals from the widest variety of industry thought leaders.
ArcGIS
AUGUST 12, 2024
Some things to consider when making a thematic map.

Confluent
AUGUST 12, 2024
Learn how Skai, an omnichannel advertising platform, revamped its architecture for effectively migrating Kafka to the cloud with Confluent.

Precisely
AUGUST 12, 2024
Key Takeaways Legacy CCM systems are damaging to customer satisfaction and employee productivity and are no longer sustainable. Boost employee morale and customer loyalty with a unified customer experience platform (CXP) that streamlines workflows and improves communication. Modern CXPs support seamless omnichannel communications, advanced capabilities like AI and ML, and ensure regulatory compliance.
RandomTrees
AUGUST 12, 2024
In today’s fast-paced business environment, data is the lifeblood of decision-making. Organizations are increasingly relying on data analytics to gain insights, drive strategies, and stay ahead of the competition. However, the complexity of data analysis often requires significant time and expertise. This is where Power BI Copilot, a cutting-edge feature from Microsoft, comes into play, revolutionizing how businesses approach data analysis.

Speaker: Alex Salazar, CEO & Co-Founder @ Arcade | Nate Barbettini, Founding Engineer @ Arcade | Tony Karrer, Founder & CTO @ Aggregage
There’s a lot of noise surrounding the ability of AI agents to connect to your tools, systems and data. But building an AI application into a reliable, secure workflow agent isn’t as simple as plugging in an API. As an engineering leader, it can be challenging to make sense of this evolving landscape, but agent tooling provides such high value that it’s critical we figure out how to move forward.
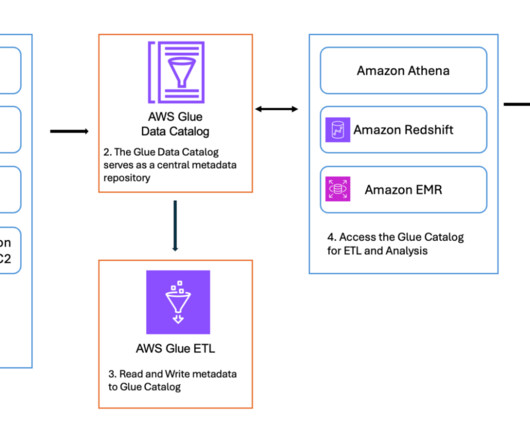
Hevo
AUGUST 12, 2024
Cloud Technology has revolutionized the way businesses manage and process data. In the previous era, there was a high demand for hardware to store and manage data, but that comes with a cost and requires highly experienced people to manage it.

Edureka
AUGUST 12, 2024
ARP spoofing, is a cyber attack in which the attacker can eavesdrop on data communication between two connected devices. With this, many risks are involved, given that this attack can be used to steal sensitive information, including passwords and credit card numbers. It can also serve as a stepping stone for more sophisticated attacks, such as man-in-the-middle and denial-of-service attacks.
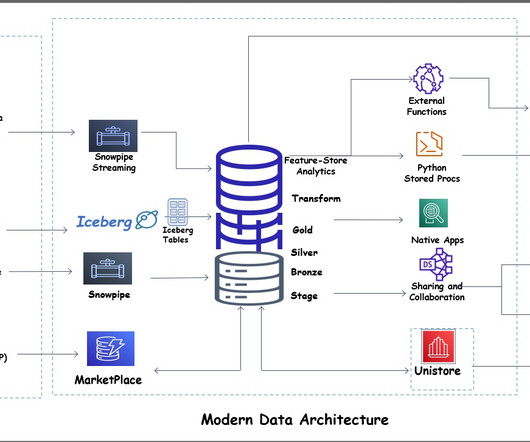
Hevo
AUGUST 12, 2024
Data professionals such as data engineers, scientists, and developers often use various tools and programming languages to get their work done. For your organization, these preferences can lead to overly complicated architecture, increased maintenance and operating costs, and new data silos that expose the data to security risk.

Edureka
AUGUST 12, 2024
Modern-day living is digital, and with this, passwords have become the keys to our virtual lives. The more dependent people become on them, the more passwords also become one of the favorite targets of malicious attackers. These attackers think of ingenious ways to crack a password and gain entry into the system. Password cracking, commonly referred to as password hacking, is defined as working out or retrieving passwords from stored or transmitted data.

Speaker: Andrew Skoog, Founder of MachinistX & President of Hexis Representatives
Manufacturing is evolving, and the right technology can empower—not replace—your workforce. Smart automation and AI-driven software are revolutionizing decision-making, optimizing processes, and improving efficiency. But how do you implement these tools with confidence and ensure they complement human expertise rather than override it? Join industry expert Andrew Skoog as he explores how manufacturers can leverage automation to enhance operations, streamline workflows, and make smarter, data-dri

Edureka
AUGUST 12, 2024
What Is Privilege Escalation? Privilege escalation is a type of cyber attack that occurs when attackers obtain increased access levels. For example, a regular computer user can become an administrator. It is extremely dangerous because it enables the thief to steal information, change settings, or destroy things. Privilege escalations are one of the concerns in cyber security.
Let's personalize your content