Enroll in a Data Science Undergraduate Program For Free
KDnuggets
JANUARY 19, 2024
Path to a Free Self-Taught Education in Data Science for Everyone.

KDnuggets
JANUARY 19, 2024
Path to a Free Self-Taught Education in Data Science for Everyone.

Knowledge Hut
JANUARY 19, 2024
"Data is the pollution problem of the information age, and protecting privacy is the environmental challenge" — Bruce Schneier. Ethical hacking is the heads-on solution for this challenge — a way to counter attacks from unwanted sources. It judges the security wall of a system and discovers and eliminates inconsistencies. Ethical hacking aims to prevent digital threats and vulnerabilities in the system and is a crucial online asset for security.

KDnuggets
JANUARY 19, 2024
Want to refresh your SQL skills? Bookmark these useful cheat sheets covering SQL basics, joins, window functions, and more.
LinkedIn Engineering
JANUARY 19, 2024
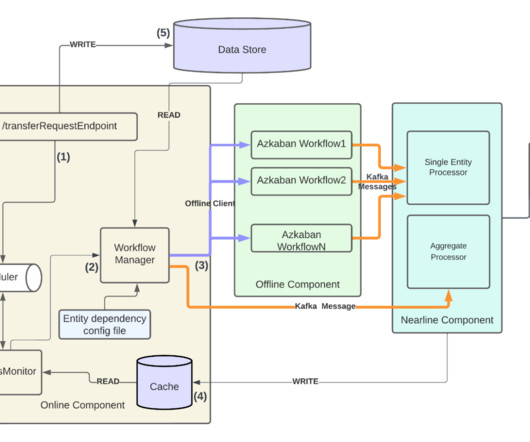
Co- Authors: Aditya Hedge and Saumi Bandyopadhyay 2022 was a year driven by change for the Talent Acquisition industry, with nearly 50k company mergers and acquisitions completed worldwide. As of November 2023, roughly 150K+ recruiters switched jobs in the previous 12 months as shown in Figure 1. These changes – whether at an organization level or a user level – result in ownership transfers of hiring entities.

Advertisement
Whether you’re creating complex dashboards or fine-tuning large language models, your data must be extracted, transformed, and loaded. ETL and ELT pipelines form the foundation of any data product, and Airflow is the open-source data orchestrator specifically designed for moving and transforming data in ETL and ELT pipelines. This eBook covers: An overview of ETL vs.
Cloudera
JANUARY 19, 2024
As described in our recent blog post , an SQL AI Assistant has been integrated into Hue with the capability to leverage the power of large language models (LLMs) for a number of SQL tasks. It can help you to create, edit, optimize, fix, and succinctly summarize queries using natural language. This is a real game-changer for data analysts on all levels and will make SQL development faster, easier, and less error-prone.

Rockset
JANUARY 19, 2024
Data mutability is the ability of a database to support mutations (updates and deletes) to the data that’s stored inside it. It’s a critical feature, especially in real-time analytics where data constantly changes and you need to present the latest version of that data to your customers and end users. Data can arrive late, it can be out of order, it can be incomplete or you might have a scenario where you need to enrich and extend your datasets with additional information for them to be complete
Data Engineering Digest brings together the best content for data engineering professionals from the widest variety of industry thought leaders.

Monte Carlo
JANUARY 19, 2024
You know those little disclaimers you always see about past performance not being indicative of future results? Well, the same goes for your data. Just because it looked good yesterday doesn’t mean it’ll hold up tomorrow – and that’s why we’re talking about data integrity testing today. Data integrity testing is the process of ensuring data is fit for the task at hand and available to only those who should have access.
Knowledge Hut
JANUARY 19, 2024
One of the first and most crucial steps in any Six Sigma project is chalking out a Six Sigma project charter. The document offers a project overview and acts as a contract between management and the Six Sigma team outlining the anticipated project results. It contains a detailed explanation of accountability as well as the roles and obligations of the team.
Knowledge Hut
JANUARY 19, 2024
Application Programming Interface (API) mania has spread throughout the globe. For scalability and reusability, it provides an interface that allows the interaction between two programs, which is crucial. For proprietary online applications or services, public APIs are becoming more frequent. Using this, other developers may simply incorporate features such as Social Media Login and Credit Card Debt Tracking with their own apps Node.js development methodologies integrate flawlessly with the Repr
Knowledge Hut
JANUARY 19, 2024
In today's business world, you need to be able to act quickly and make decisions that will keep your company moving forward. The key has the right tools, starting with knowing what data is important for your business. Business intelligence (BI) and business analytics (BA) are two terms that are often used interchangeably, but there is some important difference between business intelligence and business analytics.

Speaker: Tamara Fingerlin, Developer Advocate
In this new webinar, Tamara Fingerlin, Developer Advocate, will walk you through many Airflow best practices and advanced features that can help you make your pipelines more manageable, adaptive, and robust. She'll focus on how to write best-in-class Airflow DAGs using the latest Airflow features like dynamic task mapping and data-driven scheduling!

Knowledge Hut
JANUARY 19, 2024
Data visualization of data through graphs like charts, infographics, plots, animations, etc. The process helps translate information into a visual context to make it easier for the human brain to understand. Data visualization aims to help you identify patterns, trends, and data sets. It is one of the most significant steps of the data science projects after the data gets collected, processed, and modeled for multiple purposes.

Knowledge Hut
JANUARY 19, 2024
Business Intelligence Analyst Importance The proliferation of IoT-connected objects, IoT-based sensors, rising internet usage, and sharp increases in social media activity are all enhancing businesses' ability to gather enormous amounts of data. Many business analysts view data as the "new oil" that fuels organizational efficiency in the information age and enhances experiences, performance, and profitability.

Knowledge Hut
JANUARY 19, 2024
The market has become more competitive than ever due to the introduction of technology and changing trends. As a result, there are multiple options for businesses in a similar domain, each claiming to offer the best possible facilities. So, to stay put in the competition, business owners should make the best efforts to stand out and keep their customers glued.

Knowledge Hut
JANUARY 19, 2024
A Master of Business Administration (MBA) degree has been a prestigious qualification for many years & continues to hold value in the global job market. Pursuing an MBA opens up various career opportunities after MBA, not limited to specific industries or job profiles. Though the obvious choice for MBA graduates is corporate management, there are many more exciting career prospects after MBA to choose from.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Knowledge Hut
JANUARY 19, 2024
Entering the world of data science is a strategic move in the 21st century, known for its lucrative opportunities. With businesses relying heavily on data, the demand for skilled data scientists has skyrocketed. In data science, we use various tools, processes, and algorithms to extract insights from structured and unstructured data. Recognizing the growing need for data scientists, institutions worldwide are intensifying efforts to meet this demand.

Knowledge Hut
JANUARY 19, 2024
People now see hackers as crooks and thieves, so it's difficult to picture the term "hacker" having positive connotations. But being a hacker wasn't always a negative thing. People first used the term in a modern context at the prestigious Massachusetts Institute of Technology (MIT). Hacking was a word popularized by engineering students in the 1960s to describe the process of finding new methods to improve systems and devices to make them work more effectively.

Knowledge Hut
JANUARY 19, 2024
Cloud is a niche in technology in which security is the prime factor. This technology’s perks have made it essential for organizations to switch to cloud networks and improve performance. Moreover, security of the data and network privacy were a few other factors that boosted this inclination towards cloud switch. Now, if security is the highlight, there is a need for experts who can manage and make necessary changes to the network, standing tall on all the security expectations.

Knowledge Hut
JANUARY 19, 2024
Have you ever experienced a time when your device or personal computer or laptop was working fine one day and then stopped suddenly? If you could not find a reason why this happened, you were most likely the target of a Ransomware attack. If you notice your system missing essential files without you doing anything, this is the first sign that someone is trying to do something nefarious with your system.
Advertisement
Large enterprises face unique challenges in optimizing their Business Intelligence (BI) output due to the sheer scale and complexity of their operations. Unlike smaller organizations, where basic BI features and simple dashboards might suffice, enterprises must manage vast amounts of data from diverse sources. What are the top modern BI use cases for enterprise businesses to help you get a leg up on the competition?

Knowledge Hut
JANUARY 19, 2024
The CCSP credential is one of the most advanced cloud security credentials. To become a Certified Cloud Security Professional, you must demonstrate that you have the knowledge and technical abilities to build, manage, and secure applications, infrastructure, and information on a cloud platform. You must also be ready to put in place the industry’s best practices, policies, and processes to ensure the greatest level of security feasible.

Knowledge Hut
JANUARY 19, 2024
Certifications have always been the first choice of professionals to brush up on their knowledge and scale up in their professional careers. Like every other field, system security also has specialized certifications that people do to prove their worth to the employer and grab the best job opportunities. The International Information System Security Certification Consortium offers some certifications to the professionals like CISSP ISSMP.

Knowledge Hut
JANUARY 19, 2024
In this highly competitive world, you must stay updated and find ways to help you take your career forward. If you are working in the field of cyber security, then there are certain certification courses that you should pursue that help you acquire a certain skill set, which, in turn, can boost your career prospects. One such certification is Certified Information Systems Security Professional or CISSP in short.

Knowledge Hut
JANUARY 19, 2024
Choosing between CISA and CISM can be overwhelming. While the CISM certification trains you in Information Security Programs, the CISA certification teaches you how to best monitor, manage and defend the information system in your business. Making a wise choice out of such perplexity can be more daunting than it appears. Besides, any uninformed choices will leave you with a heavy loss of time and money.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.

Knowledge Hut
JANUARY 19, 2024
The Certified Cloud Security Professional (CCSP) credential is for experienced IT professionals with at least five years of industry experience, three of which must be in information security and one year in one of the six CCSP domains. The International Information Systems Security Certification Consortium, or ISC 2 is a non-profit organization that offers security training and certification.

Knowledge Hut
JANUARY 19, 2024
Before we look into the CISSP endorsement process, a CISSP requirement, it's vital to know what a CISSP is (ISC)2. It is a worldwide nonprofit membership society, and perhaps the world's premier cybersecurity professional organization, created the Certified Information Security Systems Professional (CISSP) Certification in 1994. Its purpose is to verify professional experience in information security and practical knowledge of security concepts and procedures.

Knowledge Hut
JANUARY 19, 2024
An ethical hacking degree has revealed rewarding employment options for many people, and a good reason. Ethical hacking, also known as penetration testing, enters or penetrates systems or networks to identify hazards and vulnerabilities that a malevolent attacker could exploit, resulting in data loss, financial loss, or other substantial changes. It never gets boring, increases demand, pays you well, and gives you a sense of accomplishment.

Knowledge Hut
JANUARY 19, 2024
These days, organizations actively seek candidates who hold the CCSP and Cisco Certifications. There are many training options, but these programs effectively demonstrate a candidate’s expertise in Cloud and IT security, validating their skills. Public clouds are dynamic and constantly changing, with many organizations shifting to multi-cloud environments.

Speaker: Jay Allardyce, Deepak Vittal, Terrence Sheflin, and Mahyar Ghasemali
As we look ahead to 2025, business intelligence and data analytics are set to play pivotal roles in shaping success. Organizations are already starting to face a host of transformative trends as the year comes to a close, including the integration of AI in data analytics, an increased emphasis on real-time data insights, and the growing importance of user experience in BI solutions.

Knowledge Hut
JANUARY 19, 2024
It is difficult for a layperson to understand ethical hacking practices, preventive countermeasures, and attack vendors. Often business owners do not know how to set up a secure infrastructure to defend against hacker attacks. It is where the Certified Ethical Hacker (CEH) training comes in handy. It teaches you how a hacker will think and act when attacking a system by providing an understanding of its weaknesses and vulnerabilities.

Knowledge Hut
JANUARY 19, 2024
CISM is a credential issued by ISACA (Information Systems Audit and Control Association) that certifies a person's ability to oversee and manage an enterprise's information security teams. It is designed for IT professionals pursuing management positions in the industry. It is one of the best web security certification programs available. Although the certification is not as technical as ISACAs other offerings, the first-time pass rate ranges between 50 and 60 percent.

Knowledge Hut
JANUARY 19, 2024
It's no wonder that technology has become an important part of our lives; consequently, its use has grown exponentially in the current business world. If you are desperate to explore new things and love to be in the IT industry, then Certified Information Systems Auditor (CISA) is one of the great career options you can have. This article will discuss what is CISA and what all are the things you must know about CISA domains.

Knowledge Hut
JANUARY 19, 2024
We live in a digital world where each passing year brings in a rapid disruption of technology. This leads to several businesses storing their privileged information online using cloud-based technology. Adding data online has led to many businesses being wary of certain security flaws that could lead to hackers infiltrating this information. This change has increased the need for cybersecurity today.

Advertisement
Explore how enterprises can enhance developer productivity and onboarding by adopting self-hosted Cloud Development Environments (CDEs). This whitepaper highlights the simplicity and flexibility of cloud-based development over traditional setups, demonstrating how large teams can leverage economies of scale to boost efficiency and developer satisfaction.
Let's personalize your content