10 Data Analyst Interview Questions to Land a Job in 2024
KDnuggets
JULY 11, 2024
Here’s how to ace your data analyst interview and land your first job.

KDnuggets
JULY 11, 2024
Here’s how to ace your data analyst interview and land your first job.

Snowflake
JULY 11, 2024
Leaders in the advertising, media and entertainment industries know all too well the importance of the media supply chain. It’s the backbone that keeps things running smoothly, including everything from content creation and management to content distribution and analytics. But media supply chains are becoming more complex to manage for several reasons.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

KDnuggets
JULY 11, 2024
Learn data science through interactive courses, books, guides, code examples, projects, and free courses based on top university curricula. Also, access interview questions and best practices.

Uber Engineering
JULY 11, 2024
Modernizing the fundamentals of log management at Uber: How we used CLP to build a new logging infra that lets users view and analyze their logs seamlessly, at scale!

Advertisement
In Airflow, DAGs (your data pipelines) support nearly every use case. As these workflows grow in complexity and scale, efficiently identifying and resolving issues becomes a critical skill for every data engineer. This is a comprehensive guide with best practices and examples to debugging Airflow DAGs. You’ll learn how to: Create a standardized process for debugging to quickly diagnose errors in your DAGs Identify common issues with DAGs, tasks, and connections Distinguish between Airflow-relate

Confluent
JULY 11, 2024
confluent-kafka-javascript offers two APIs for calling Kafka from JS, one KafkaJS-like & one node-rdkafka-like. Learn it by making an app w/producer, consumer & UI.

KDnuggets
JULY 11, 2024
Let's explore how you can harness BigQuery's capabilities and dive into industry use cases where anomaly detection is making a real difference.
Data Engineering Digest brings together the best content for data engineering professionals from the widest variety of industry thought leaders.

Ascend.io
JULY 11, 2024
Metadata is the information that provides context and meaning to data, ensuring it’s easily discoverable, organized, and actionable. It enhances data quality, governance, and automation, transforming raw data into valuable insights. Imagine a library with millions of books but no catalog system to organize them. Chaos, right? This is what managing data without metadata feels like.
Scott Logic
JULY 11, 2024
As we keep on building the InferGPT chatbot internally at Scott Logic, the task of crafting prompts is one that our team is experimenting with, and through iterative testing and analysis, we’re getting a sense of the techniques that return the best results. Whether that’s prompting an agent to write a Cypher query or to select the right tool for the task at hand, even the smallest changes and refinements in prompts are changing the accuracy of the responses we get back.

Striim
JULY 11, 2024
Fraud is on the rise in the financial sector, with the Federal Trade Commission reporting a staggering $10 billion in losses for 2023 alone. This marks a 14% increase from 2022, underscoring the escalating threat of fraudulent activity within the industry. This increase can largely be attributed to the increased usage of instant transaction technologies and mobile payments.

Knowledge Hut
JULY 11, 2024
Do you have dreams of becoming a software engineer? Do you wonder if a software engineer career is worthwhile? Analyze the pros and cons of being a software engineer before choosing the path. Almost every industry employs software developers today. Creating software applications has become increasingly important as the world becomes more digitized. But there are also various advantages and disadvantages of software engineering.

Speaker: Tamara Fingerlin, Developer Advocate
Apache Airflow® 3.0, the most anticipated Airflow release yet, officially launched this April. As the de facto standard for data orchestration, Airflow is trusted by over 77,000 organizations to power everything from advanced analytics to production AI and MLOps. With the 3.0 release, the top-requested features from the community were delivered, including a revamped UI for easier navigation, stronger security, and greater flexibility to run tasks anywhere at any time.

Uber Engineering
JULY 11, 2024
SLATE is revolutionizing microservice development by adding robust debugging capabilities to our E2E testing framework. Developers can now seamlessly debug in production or locally with production dependencies, boosting productivity and issue resolution. Dive into the details in our latest blog post!

Edureka
JULY 11, 2024
The Man-in-the-Middle attack is a cyber attack. In this attack, an attacker eavesdrops on a conversation or transaction that takes place. The attacker can either modify or delete the information. This is a dangerous kind of attack which poses a risk to business entities and individuals. The key point about man in the middle attack (MitM) is that they can occur on any network regardless of its type.

Uber Engineering
JULY 11, 2024
Discover how Uber ensures uninterrupted service with Cassandra’s multi-zone configuration, designed to withstand failures in any single zone.
Monte Carlo
JULY 11, 2024
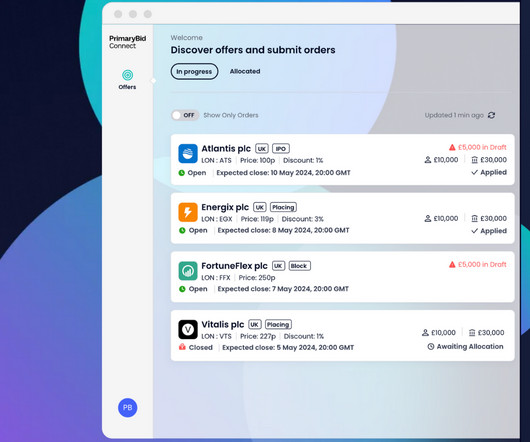
London-based PrimaryBid is on a mission: creating greater fairness, inclusion, and retail access to capital market transactions. Their fintech platform helps companies connect retail investors to capital market transactions like IPOs, follow-on fundraisings, and debt raises at the same time and price as institutional investors. That requires operating in a regulated industry and ensuring real-time, secure access to sensitive financial transaction data.

Speaker: Alex Salazar, CEO & Co-Founder @ Arcade | Nate Barbettini, Founding Engineer @ Arcade | Tony Karrer, Founder & CTO @ Aggregage
There’s a lot of noise surrounding the ability of AI agents to connect to your tools, systems and data. But building an AI application into a reliable, secure workflow agent isn’t as simple as plugging in an API. As an engineering leader, it can be challenging to make sense of this evolving landscape, but agent tooling provides such high value that it’s critical we figure out how to move forward.
Let's personalize your content