Introducing AI/BI: Intelligent Analytics for Real-World Data
databricks
JUNE 11, 2024
Today, we are excited to announce Databricks AI/BI , a new type of business intelligence product built from the ground up to deeply.

databricks
JUNE 11, 2024
Today, we are excited to announce Databricks AI/BI , a new type of business intelligence product built from the ground up to deeply.
ArcGIS
JUNE 11, 2024
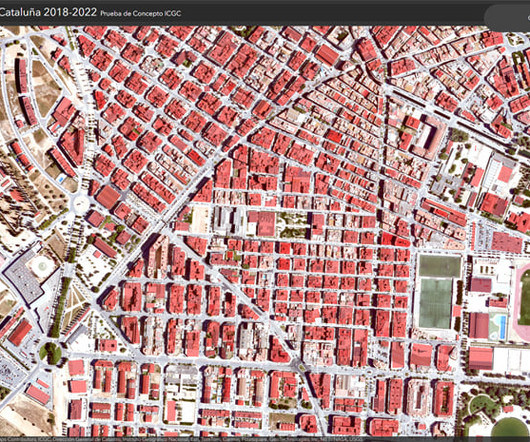
Revolutionizing GIS: Streamlining Change Detection for Mapping Agencies.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Snowflake
JUNE 11, 2024
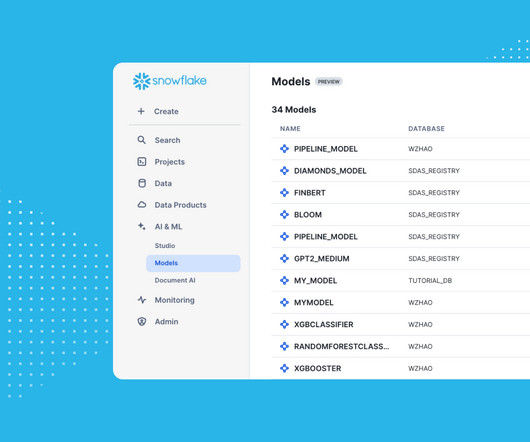
Bringing machine learning (ML) models into production is often hindered by fragmented MLOps processes that are difficult to scale with the underlying data. Many enterprises stitch together a complex mix of various MLOps tools to build an end-to-end ML pipeline. The friction of having to set up and manage separate environments for features and models creates operational complexity that can be costly to maintain and difficult to use.

ArcGIS
JUNE 11, 2024
The Living Atlas team publishes a lot of web layers. Here's some of our favorite tips and tricks for customizing your layers and maps.

Advertisement
In Airflow, DAGs (your data pipelines) support nearly every use case. As these workflows grow in complexity and scale, efficiently identifying and resolving issues becomes a critical skill for every data engineer. This is a comprehensive guide with best practices and examples to debugging Airflow DAGs. You’ll learn how to: Create a standardized process for debugging to quickly diagnose errors in your DAGs Identify common issues with DAGs, tasks, and connections Distinguish between Airflow-relate

KDnuggets
JUNE 11, 2024
Improve your skills, creativity, and renown by participating in competitions.

Confessions of a Data Guy
JUNE 11, 2024
One of the things I love about Python is its flexibility and huge community, a community that puts out a never-ending stream of useful packages for the average Software Engineer. In a show of solidarity to the open-source community, I thought I would publish a PYPI package that will probably be used by 5 people […] The post Building Open-Source Python Packages – SparklePop appeared first on Confessions of a Data Guy.
Data Engineering Digest brings together the best content for data engineering professionals from the widest variety of industry thought leaders.

Cloudera
JUNE 11, 2024
More than two-thirds of companies are currently using Generative AI (GenAI) models, such as large language models (LLMs), which can understand and generate human-like text, images, video, music, and even code. However, the true power of these models lies in their ability to adapt to an enterprise’s unique context. By leveraging an organization’s proprietary data, GenAI models can produce highly relevant and customized outputs that align with the business’s specific needs and ob

Engineering at Meta
JUNE 11, 2024
MobileConfig enables developers to centrally manage a mobile app’s configuration parameters in our data centers. Once a parameter value is changed on our central server, billions of app devices automatically fetch and apply the new value without app updates. These remotely managed configuration parameters serve various purposes such as A/B testing, feature rollout, and app personalization.

Confluent
JUNE 11, 2024
Use Confluent’s data streaming platform to bring real-time insights to customer loyalty programs, creating personalized offers that drive greater retention and revenue.
ArcGIS
JUNE 11, 2024
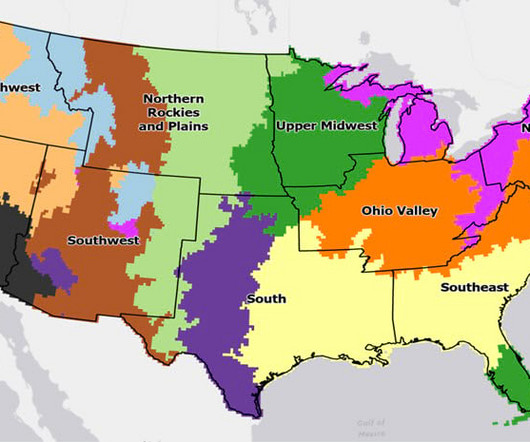
This is the fifth in a series of blogs that showcase an end-to-end spatial data science workflow for clustering US precipitation regions.

Speaker: Tamara Fingerlin, Developer Advocate
Apache Airflow® 3.0, the most anticipated Airflow release yet, officially launched this April. As the de facto standard for data orchestration, Airflow is trusted by over 77,000 organizations to power everything from advanced analytics to production AI and MLOps. With the 3.0 release, the top-requested features from the community were delivered, including a revamped UI for easier navigation, stronger security, and greater flexibility to run tasks anywhere at any time.

Confluent
JUNE 11, 2024
Build with Confluent helps system integrators develop joint solutions faster, including specialized software bundles, support from data streaming experts to certify offerings, and access to Confluent’s Go-To-Market teams to amplify audience.

Cloudyard
JUNE 11, 2024
Read Time: 1 Minute, 48 Second RETRY LAST: In modern data workflows, tasks are often interdependent, forming complex task chains. Ensuring the reliability and resilience of these workflows is critical, especially when dealing with production data pipelines. Imagine you’re tasked with managing a critical data pipeline in Snowflake that processes and transforms large datasets.
Striim
JUNE 11, 2024
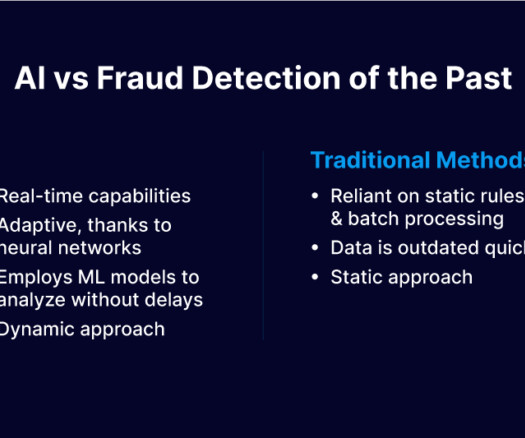
In today’s fast-paced financial landscape, robust security measures are not optional — they are essential. Financial services organizations face a constant onslaught of fraud attempts that threaten both their bottom line and the trust of their customers. That’s where real-time AI-powered fraud detection comes into the picture. Think of it as a game-changing solution designed to safeguard transactions and maintain customer confidence.

DareData
JUNE 11, 2024
In this post, we’ll learn how to train a computer vision model using a convolutional Neural Network in PyTorch PyTorch is currently one of the hottest libraries in the Deep Learning field. Used by thousand of developers around the world, the library gained prominence since the release of ChatGPT and the introduction of deep learning into mainstream news headlines.

Speaker: Alex Salazar, CEO & Co-Founder @ Arcade | Nate Barbettini, Founding Engineer @ Arcade | Tony Karrer, Founder & CTO @ Aggregage
There’s a lot of noise surrounding the ability of AI agents to connect to your tools, systems and data. But building an AI application into a reliable, secure workflow agent isn’t as simple as plugging in an API. As an engineering leader, it can be challenging to make sense of this evolving landscape, but agent tooling provides such high value that it’s critical we figure out how to move forward.

Knowledge Hut
JUNE 11, 2024
In a digital era brimmed with interconnected devices, cybercrimes and security breach incidents have become ever so common, threatening the privacy and security of the users. The recent introduction of amenities such as ubiquitous internet access, the internet of things (IoT), and cloud computing to the general masses has inspired a new cybercrime wave, which has led security experts to make considerable advancements in digital forensics in order to keep up with evolving cyber-crimes.

Knowledge Hut
JUNE 11, 2024
Ethical hacking is a method I've used to test website and application security by simulating attacks, and it serves the crucial purpose of identifying and rectifying vulnerabilities before malicious actors can exploit them. Whether provided as a free service or part of a paid contract, it's indispensable for companies and individuals to safeguard their accounts.

Knowledge Hut
JUNE 11, 2024
In recent years, Machine Learning, Artificial Intelligence, and Data Science have become some of the most talked-about technologies. These technological advancements have enabled businesses to automate and operate at a much higher level. Companies of all sizes are investing millions of dollars in data analysis and on professionals who can build these exceptionally powerful data-driven products.
Let's personalize your content